Published on : Jan 9, 2017
Category : Microsoft Azure
With the release of version 8.1, BizTalk360 has the capability of monitoring
Logic Apps, API Apps and Azure Service Bus in the Microsoft Azure stack. During the development phase, we have faced quite some challenges to bring Azure settings into on-premise BizTalk360.
In this article, we can see how BizTalk360 adopted the Azure Service Management API.
Connecting to Azure Service Management API’s
There are two options available to programmatically connect to Azure Service Management API’s:
- Azure Management Certificate
- Azure Active Directory
Let’s take a detailed look at the options below.
Azure Management Certificate
API Apps use Management Certificates to authenticate and retrieve the details.
To connect the API’s using Management Certificates, we have to generate and download the certificate from Azure. Next, you’ll convert the downloaded file to a X509Certificate2 and attach this certificate under the
WebRequestHandler.ClientCertificates in web requests to get the results.
- Download the Azure Setting file https://manage.windowsazure.com/publishsettings/index?client=xplat.If you click on the link and login into Azure portal, the Settings file will be downloaded instantly.
- After opening that file, you can find the subscription with ID and you will be able to manage the certificate. Just parse that certificate using a C# XML class and convert it into a X509Certificate2.
var certificateAsBytes = Convert.FromBase64String(certificateString);
var certificate = new X509Certificate2(certificateAsBytes);
- Once the certificate is ready, the next step is to insert the certificate into a HTTP Handler. Then you can call an Azure API using that handler.
Azure Active Directory
Logic Apps use Azure Active Directory authentication.
If the Azure subscription is not connected with an Azure Active Directory, you’ll have to create a new Active Directory in Azure and get a ClientID, Appkey and TenantID to call the Azure API’s.
We can see an example how Logic Apps information are retrieved using Azure Active Directory.
private static string azureActiveDirectorylnstance =
System.Configuration.ConfigurationManager.AppSettings["AzureActiveDirectoryInstance"];
private static string tenantlD =
System.Configuration.ConfigurationManager.AppSettings["TenantlD"];
private static string clientlD =
System.Configuration.ConfigurationManager.AppSettings["ClientID"];
private static string appKey =
System.Configuration.ConfigurationManager.AppSettings("AppKey"];
private static string resource =
System.Configuration.ConfigurationManager.AppSettings["Resource"];
private static string subscriptionlD =
System.Configuration.ConfigurationManager.AppSettings["SubscriptionID"];
static string authority = azureActiveDirectorylnstance + tenantlD;
private void buttonl_Click(object sender, EventArgs e)
{
using (LogicManagementClient client = GetLogicManagementClient())
var workflowPage = client.Workflows.ListBySubscription();
List<Workflows> workflows = workFlowPage.ToList();
Foreach (var workflow in workflows)
listboxl. Items.Add(workflow.Name);
}
private string GetToken()
{
var httpClient = new HttpClient();
var authContext = new AuthenticationContext(authority);
var clientCredential = new ClientCredential(clientID, appKey);
var result = authContext.AcquireToken(resource, clientCredential);
return result.AccessToken;
}
private string GetAuthToken()
{
var httpClient = new HttpClient();
var authContext = new AuthenticationContext(authority);
var clientCredential = new ClientCredential(clientID, appKey);
var result = authContext.AcquireToken(resource, clientCredential);
var token = result.CreateAuthorizationHeader();
return token;
}
private LogicManagementClient GetLogicManagementClient()
{
var credentials = new TokenCredentials(GetToken());
var client = new LogicManagementClient(credentials);
client.SubscriptionId = subscriptionID;
return client;
}
Proxy Settings
If the environment is configured with Proxy Settings, you’ll have to modify the Access Token code by using HttpWebRequest instead of HttpClient, since we have to support a Proxy to all the service calls.
HttpWebRequest request = (HttpWebRequest)WebRequest.Create(String.Format(subscriptionsAuthorizationUri, subscription.TentantId));
System.Text.ASCIIEncoding encoding = new System.Text.ASCIIEncoding();
string postData = "grant_type=client_credentials";
postData += "&resource=" + HttpUtility.UrlEncode(resource);
postData += "&client_id=" + HttpUtility.UrlEncode(subscription.ClientId);
postData += "&client_secret=" + HttpUtility.UrlEncode(subscription.SecretKey);
byte[] data = encoding.GetBytes(postData);
request.Method = "POST";
request.ContentType = "application/x-www-form-urlencoded";
request.ContentLength = data.Length;
if (webProxy != null)
{
request.Proxy = webProxy;
}
using (Stream stream = request.GetRequestStream())
{
stream.Write(data, 0, data.Length);
}
using (var response = request.GetResponse())
{
using (var stream = response.GetResponseStream())
{
DataContractJsonSerializer ser = new DataContractJsonSerializer(typeof(B360.Plugin.Common.AADJWTToken));
B360.Plugin.Common.AADJWTToken token = (B360.Plugin.Common.AADJWTToken)(ser.ReadObject(stream));
return token.AccessToken;
}
}
Azure Subscription Configuration
Now, let us see how BizTalk360 validates Azure credentials and
configure the Azure subscription.
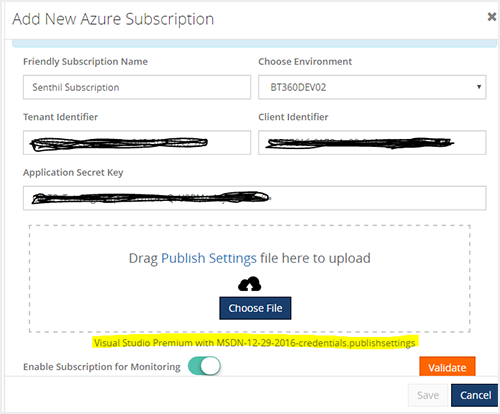
Call the Azure Role Access API to ensure that BizTalk360 has permission to access the Azure resources.
roleAssignmentsURI = "https://management.azure.com/{0}/providers/Microsoft.Authorization/roleAssignments?api-version={1}&$filter={2}";
When we call this API using the generated token, we will get multiple responses — so we are handling all the responses properly at the code to complete the validation.
Forbidden
response.StatusCode == HttpStatusCode.Forbidden
If the Validation method returns Forbidden, then that means the details provided are right. However, BizTalk360 doesn’t have access to read those resources. In this case, we will generate a PowerShell command and prompt the user to execute that command in PowerShell and then try to validate again. If they executed that command and tried to validate again, we will get a OK response and close.
azurePowerShellCommand = "New-AzureRmRoleAssignment -ObjectId '{0}' -RoleDefinitionName Owner -Scope '/subscriptions/{1}'";
Not Found
response.StatusCode == HttpStatusCode.NotFound
If the Service responds with Not Found status code, then redirect back to user saying there is a mismatch in the provided Azure Active Directory and the Management Certificate.
OK
response.StatusCode == HttpStatusCode.OK
When the response returns OK, this confirms the Azure Subscription validation is successfully completed and configured into BizTalk360.
 Call the Azure Role Access API to ensure that BizTalk360 has permission to access the Azure resources.
Call the Azure Role Access API to ensure that BizTalk360 has permission to access the Azure resources.